| welcome! page:server/apache/openssl.html | |
| |
|
| | |
| home:topへ server library:top へ | |
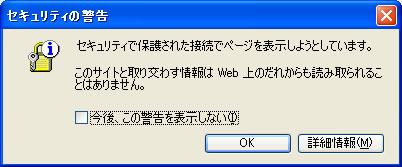
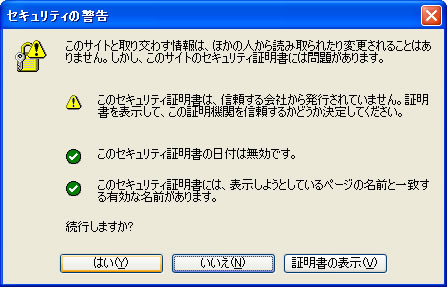
# If you are using SSL please uncommented the next line
HTTPDOPT=-DSSL
# rm -f /etc/httpd/conf/ssl/ssi.key/server.key 
# rm -f /etc/httpd/conf/ssl/ssi.crt/server.crt 
# cd /etc/httpd/conf/ssl/ssl.key# /usr/bin/openssl genrsa -des3 1024 > /etc/httpd/conf/ssl/ssl.key/server.key
warning, not much extra random data, consider using the -rand option Generating RSA private key, 1024 bit long modulus ...................................................++++++ .........++++++ e is 65537 (0x10001) Enter PEM pass phrase:**********
//パスワードの入力(エコーされない) Verifying password - Enter PEM pass phrase:*********
//もう一度入力(エコーされない) //Apache起動の関係で、毎回パスワードを入力しないでいい設定をします。 # openssl rsa -in server.key -out server.key
read RSA key Enter PEM pass phrase:
//上記のパスワードの入力(エコーされない) writing RSA key
# openssl req -new -key server.key -out ../ssl.csr/server.csrUsing configuration from /var/ssl/openssl.cnf You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:JP
State or Province Name (full name) [Some-State]:Osaka
Locality Name (eg, city) []:Yao
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Odic
//組織名です Organizational Unit Name (eg, section) []:Web
//部門名です Common Name (eg, YOUR name) []:www.******.co.jp
//サーバ名です(DNSに登録している名前) Email Address []:tako@******.co.jp
//サーバ管理者mailアドレス Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:
//無視 An optional company name []:
//無視 //server.csrとserver.key暗号鍵ファイルで証明書を作成します # openssl x509 -in ../ssl.csr/server.csr -out ../ssl.crt/server.crt -req -signkey ./server.key
Signature ok subject=/C=JP/ST=Osaka/L=Yao/O=Odic/OU=Web/CN=www.******.co.jp/Email=tako@******.co.jp. //先の入力データ Getting Private key
##### Section 3: Virtual Hosts ######
#
# VirtualHost: If you want to maintain multiple domains/hostnames on your
# machine you can setup VirtualHost containers for them. Most configurations
# use only name-based virtual hosts so the server doesn't need to worry about
# IP addresses. This is indicated by the asterisks in the directives below.
#
# Please see the documentation at <;URL:http://www.apache.org/docs/vhosts/>
# for further details before you try to setup virtual hosts.
#
# You may use the command line option '-S' to verify your virtual host
# configuration.
#
# Use name-based virtual hosting.
#
#################################
#NameVirtualHost *
#NameVirtualHost ***.***.***.***:80
NameVirtualHost ***.***.***.***:443
#
# VirtualHost example:
# Almost any Apache directive may go into a VirtualHost container.
# The first VirtualHost section is used for requests without a known
# server name.
#
# < VirtualHost *>
# ServerAdmin webmaster@dummy-host.example.com
# DocumentRoot /www/docs/dummy-host.example.com
# ServerName dummy-host.example.com
# ErrorLog logs/dummy-host.example.com-error_log
# CustomLog logs/dummy-host.example.com-access_log common
#</VirtualHost>
#<VirtualHost _default_:*>
#</VirtualHost>
##
## SSL Global Context
##
## All SSL configuration in this context applies both to
## the main server and all SSL-enabled virtual hosts.
##
#
# Some MIME-types for downloading Certificates and CRLs
#
<IfDefine SSL>
AddType application/x-x509-ca-cert .crt
AddType application/x-pkcs7-crl .crl
</IfDefine>
<IfModule mod_ssl.c>
# Pass Phrase Dialog:
# Configure the pass phrase gathering process.
# The filtering dialog program (`builtin' is a internal
# terminal dialog) has to provide the pass phrase on stdout.
SSLPassPhraseDialog builtin
# Inter-Process Session Cache:
# Configure the SSL Session Cache: First the mechanism
# to use and second the expiring timeout (in seconds).
#SSLSessionCache none
#SSLSessionCache shmht:/var/run/ssl_scache(512000)
#SSLSessionCache shmcb:/var/run/ssl_scache(512000)
SSLSessionCache dbm:/var/run/ssl_scache
SSLSessionCacheTimeout 300
# Semaphore:
# Configure the path to the mutual exclusion semaphore the
# SSL engine uses internally for inter-process synchronization.
SSLMutex file:/var/run/ssl_mutex
# Pseudo Random Number Generator (PRNG):
# Configure one or more sources to seed the PRNG of the
# SSL library. The seed data should be of good random quality.
# WARNING! On some platforms /dev/random blocks if not enough entropy
# is available. This means you then cannot use the /dev/random device
# because it would lead to very long connection times (as long as
# it requires to make more entropy available). But usually those
# platforms additionally provide a /dev/urandom device which doesn't
# block. So, if available, use this one instead. Read the mod_ssl User
# Manual for more details.
SSLRandomSeed startup builtin
SSLRandomSeed connect builtin
#SSLRandomSeed startup file:/dev/random 512
#SSLRandomSeed startup file:/dev/urandom 512
#SSLRandomSeed connect file:/dev/random 512
#SSLRandomSeed connect file:/dev/urandom 512
# Logging:
# The home of the dedicated SSL protocol logfile. Errors are
# additionally duplicated in the general error log file. Put
# this somewhere where it cannot be used for symlink attacks on
# a real server (i.e. somewhere where only root can write).
# Log levels are (ascending order: higher ones include lower ones):
# none, error, warn, info, trace, debug.
SSLLog /var/log/httpd/ssl_engine_log
SSLLogLevel info
</IfModule>
<IfDefine SSL>
##
## SSL Virtual Host Context
##
#######################################
##<VirtualHost ***.***.***.***:80>
<VirtualHost ***.***.***.***:443>
#### 初期値は <VirtualHost _default_:443> ####
# General setup for the virtual host
#### 公開する最上位ディレクトリ sslディレクトリを作成した ####
DocumentRoot "/home/*****/public_html/ssl"
#### 初期値DocumentRoot "/var/www/html" ####
ServerName localhost
#ServerName localhost
ServerAdmin root@localhost
ErrorLog /var/log/httpd/error_log
TransferLog /var/log/httpd/access_log
# SSL Engine Switch:
# Enable/Disable SSL for this virtual host.
##### このバーチャルホストでSSLを使用するかどうか ####
SSLEngine on
# SSL Cipher Suite:
# List the ciphers that the client is permitted to negotiate.
# See the mod_ssl documentation for a complete list.
#### クライアントとの通信に使用する暗号を指定 ####
SSLCipherSuite ALL:!ADH:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLv2:+EXP:+eNULL
# Server Certificate:
# Point SSLCertificateFile at a PEM encoded certificate. If
# the certificate is encrypted, then you will be prompted for a
# pass phrase. Note that a kill -HUP will prompt again. A test
# certificate can be generated with `make certificate' under
# built time. Keep in mind that if you've both a RSA and a DSA
# certificate you can configure both in parallel (to also allow
# the use of DSA ciphers, etc.)
##### サーバのSSL証明書の場所指定 ####
SSLCertificateFile /etc/httpd/conf/ssl/ssl.crt/server.crt
#SSLCertificateFile /etc/httpd/conf/ssl/ssl.crt/server-dsa.crt
# Server Private Key:
# If the key is not combined with the certificate, use this
# directive to point at the key file. Keep in mind that if
# you've both a RSA and a DSA private key you can configure
# both in parallel (to also allow the use of DSA ciphers, etc.)
##### サーバのSSL暗号鍵の場所指定 ####
SSLCertificateKeyFile /etc/httpd/conf/ssl/ssl.key/server.key
#SSLCertificateKeyFile /etc/httpd/conf/ssl/ssl.key/server-dsa.key
# Server Certificate Chain:
# Point SSLCertificateChainFile at a file containing the
# concatenation of PEM encoded CA certificates which form the
# certificate chain for the server certificate. Alternatively
# the referenced file can be the same as SSLCertificateFile
# when the CA certificates are directly appended to the server
# certificate for convinience.
##### クライアントの持っているCAとサーバが認証を受けたCAとの関係が記述 ####
##### してあるファイルを指定。CAに署名をもらった際に受け取るファイル ####
#SSLCertificateChainFile /etc/httpd/conf/ssl/ssl.crt/ca.crt
# Certificate Authority (CA):
# Set the CA certificate verification path where to find CA
# certificates for client authentication or alternatively one
# huge file containing all of them (file must be PEM encoded)
# Note: Inside SSLCACertificatePath you need hash symlinks
# to point to the certificate files. Use the provided
# Makefile to update the hash symlinks after changes.
#### 上位CAのファイルのあるディレクトリパス、またはそのファイル指定 #####
#SSLCACertificatePath /etc/httpd/conf/ssl/ssl.crt
#SSLCACertificateFile /etc/httpd/conf/ssl/ssl.crt/ca-bundle.crt
# Certificate Revocation Lists (CRL):
# Set the CA revocation path where to find CA CRLs for client
# authentication or alternatively one huge file containing all
# of them (file must be PEM encoded)
# Note: Inside SSLCARevocationPath you need hash symlinks
# to point to the certificate files. Use the provided
# Makefile to update the hash symlinks after changes.
#### クライアント認証時に拒否するCA指定 ####
#SSLCARevocationPath /etc/httpd/conf/ssl/ssl.crl
#SSLCARevocationFile /etc/httpd/conf/ssl/ssl.crl/ca-bundle.crl
# Client Authentication (Type):
# Client certificate verification type and depth. Types are
# none, optional, require and optional_no_ca. Depth is a
# number which specifies how deeply to verify the certificate
# issuer chain before deciding the certificate is not valid.
#### クライアントを認証する方法と、認証時に確認のために参照するCAの深さ指定 ####
#### none 認証しない ####
#### option 認証を受けることができる ####
#### require 認証を必要とする ####
#### option_no_ca サーバが信用しないCA(自己署名など)でも認証を受けられる ####
#### 不特定多数のアクセスを受けるのであればnone ####
SSLVerifyClient none
#SSLVerifyClient require
#SSLVerifyDepth 10
# Access Control:
# With SSLRequire you can do per-directory access control based
# on arbitrary complex boolean expressions containing server
# variable checks and other lookup directives. The syntax is a
# mixture between C and Perl. See the mod_ssl documentation
# for more details.
#### ディレクトリに対して、SSLでのアクセスコントロール指定 ####
#<Location />
#SSLRequire ( %{SSL_CIPHER} !~ m/^(EXP|NULL)/ \
# and %{SSL_CLIENT_S_DN_O} eq "Snake Oil, Ltd." \
# and %{SSL_CLIENT_S_DN_OU} in {"Staff", "CA", "Dev"} \
# and %{TIME_WDAY} >= 1 and %{TIME_WDAY} <= 5 \
# and %{TIME_HOUR} >= 8 and %{TIME_HOUR} <= 20 ) \
# or %{REMOTE_ADDR} =~ m/^192\.76\.162\.[0-9]+$/
#</Location>
#### SSLを使用する際のオプション指定 ####
# SSL Engine Options:
# Set various options for the SSL engine.
# o FakeBasicAuth:
# Translate the client X.509 into a Basic Authorisation. This means that
# the standard Auth/DBMAuth methods can be used for access control. The
# user name is the `one line' version of the client's X.509 certificate.
# Note that no password is obtained from the user. Every entry in the user
# file needs this password: `xxj31ZMTZzkVA'.
# o ExportCertData:
# This exports two additional environment variables: SSL_CLIENT_CERT and
# SSL_SERVER_CERT. These contain the PEM-encoded certificates of the
# server (always existing) and the client (only existing when client
# authentication is used). This can be used to import the certificates
# into CGI scripts.
# o StdEnvVars:
# This exports the standard SSL/TLS related `SSL_*' environment variables.
# Per default this exportation is switched off for performance reasons,
# because the extraction step is an expensive operation and is usually
# useless for serving static content. So one usually enables the
# exportation for CGI and SSI requests only.
# o CompatEnvVars:
# This exports obsolete environment variables for backward compatibility
# to Apache-SSL 1.x, mod_ssl 2.0.x, Sioux 1.0 and Stronghold 2.x. Use this
# to provide compatibility to existing CGI scripts.
# o StrictRequire:
# This denies access when "SSLRequireSSL" or "SSLRequire" applied even
# under a "Satisfy any" situation, i.e. when it applies access is denied
# and no other module can change it.
# o OptRenegotiate:
# This enables optimized SSL connection renegotiation handling when SSL
# directives are used in per-directory context.
##### コメントアウトした ####
SSLOptions +FakeBasicAuth +ExportCertData +CompatEnvVars +StrictRequire
#初期値 #SSLOptions +FakeBasicAuth +ExportCertData +CompatEnvVars +StrictRequire
#### .cgi .shtml phtml php php3で終るファイルに対するSSLのオプション ####
<Files ~ "\.(cgi|shtml|phtml|php|php3?)$">
SSLOptions +StdEnvVars
</Files>
#<Files ~ "\.(cgi|shtml|phtml|php3?)$">
# SSLOptions +StdEnvVars
#</Files>
#### /home/*****/public_html/ssl ディレクトリに対するSSLのオプション #####
<Directory "/home/*****/public_html/ssl">
SSLOptions +StdEnvVars
</Directory>
#<Directory "/var/www/cgi-bin">
# SSLOptions +StdEnvVars
#</Directory>
# SSL Protocol Adjustments:
# The safe and default but still SSL/TLS standard compliant shutdown
# approach is that mod_ssl sends the close notify alert but doesn't wait for
# the close notify alert from client. When you need a different shutdown
# approach you can use one of the following variables:
# o ssl-unclean-shutdown:
# This forces an unclean shutdown when the connection is closed, i.e. no
# SSL close notify alert is send or allowed to received. This violates
# the SSL/TLS standard but is needed for some brain-dead browsers. Use
# this when you receive I/O errors because of the standard approach where
# mod_ssl sends the close notify alert.
# o ssl-accurate-shutdown:
# This forces an accurate shutdown when the connection is closed, i.e. a
# SSL close notify alert is send and mod_ssl waits for the close notify
# alert of the client. This is 100% SSL/TLS standard compliant, but in
# practice often causes hanging connections with brain-dead browsers. Use
# this only for browsers where you know that their SSL implementation
# works correctly.
#### クライアント情報などをもとに、そのクライアントに対しての特別な設定を指定 ####
# Notice: Most problems of broken clients are also related to the HTTP
# keep-alive facility, so you usually additionally want to disable
# keep-alive for those clients, too. Use variable "nokeepalive" for this.
# Similarly, one has to force some clients to use HTTP/1.0 to workaround
# their broken HTTP/1.1 implementation. Use variables "downgrade-1.0" and
# "force-response-1.0" for this.
#### MS Internet Explolerがクライアントであれば ####
#### KeepAlive接続を無効とし ####
#### クライアントからのクローズ通知なしで接続を切ることができる、と指定。 ####
SetEnvIf User-Agent ".*MSIE.*" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
# Per-Server Logging:
# The home of a custom SSL log file. Use this when you want a
# compact non-error SSL logfile on a virtual host basis.
#### カスタムログのディレクトリと、その内容の指定 ####
CustomLog /var/log/httpd/ssl_request_log \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
</IfDefine>
/var/log/httpd/access_log {
weekly
rotate 4
missingok
postrotate
/usr/bin/killall -HUP httpd
endscript
}
/var/log/httpd/agent_log {
missingok
postrotate
/usr/bin/killall -HUP httpd
endscript
}
/var/log/httpd/error_log {
weekly
rotate 4
missingok
postrotate
/usr/bin/killall -HUP httpd
endscript
}
/var/log/httpd/referer_log {
missingok
postrotate
/usr/bin/killall -HUP httpd
endscript
}
#####ここから############################
/var/log/httpd/ssl_engine_log {
missingok
postrotate
/usr/bin/killall -HUP httpd
endscript
}
/var/log/httpd/ssl_request_log {
missingok
postrotate
/usr/bin/killall -HUP httpd
endscript
}
#####ここまでを追加####################
# rm -f /etc/httpd/conf/ssl/ssi.key/server.key 
# rm -f /etc/httpd/conf/ssl/ssi.crt/server.crt 
# rm -f /etc/httpd/conf/ssl.key/server.key 
# rm -f /etc/httpd/conf/ssl.crt/server.crt 
# rm -f /etc/httpd/conf/ssl/ssi.key/server.key 
# rm -f /etc/httpd/conf/ssl/ssi.crt/server.crt 
| 《 ■ 参照URL ※サイト内参照ページ 引用、参照書籍 ■ 》 |
| ※ OpenSSH(Secure Shell) 公開鍵と秘密鍵 |
| OpenSSL日本語サイト |
| 日本ジオトラスト株式会社 |
(02.11.02 初稿)
(03.12.23 「アクセスの手順」追記)
top home:top server library:top PHP PostgreSQL MySQL サンプルスクリプト