OpenVPN(Virtual Private Network)
はじめに ▲ top
準備 ▲ top
# modprobe tun
# mkdir /dev/net
# mknod /dev/net/tun c 10 200
# chmod 0700 /dev/net/tun
alias char-major-10-200 tun
modprobe tun
# lsmod
OpenSSL (暗号化) lzo (データの圧縮) pam (ユーザ認証)
# cd /usr/local/src
# wget http://www.oberhumer.com/opensource/lzo/download/lzo-2.02.tar.gz
# tar zxvf lzo-2.02.tar.gz
# cd lzo-2.02
# ./configure
# make
# make install
インストール ▲ top
# cd /usr/local/src
# wget http://openvpn.net/release/openvpn-2.0.9.tar.gz
# tar zxvf openvpn-2.0.9.tar.gz
# cd openvpn-2.0.9
# ./configure
# make
# make install
# which openvpn
# mkdir /etc/openvpn
# cp sample-scripts/openvpn.init /etc/openvpn
# chmod 755 /etc/openvpn/openvpn.init ←起動スクリプト
# cp /usr/local/src/openvpn-2.0.5/sample-scripts/bridge-start /etc/openvpn
# chmod 755 /etc/openvpn/bridge-start ←ブリッジ有効
# cp /usr/local/src/openvpn-2.0.5/sample-scripts/bridge-stop /etc/openvpn
# chmod 755 /etc/openvpn/bridge-stop ←ブリッジ無効
OpenVPNサーバ各種設定 ▲ top
# open up this port on your firewall.
port 5000
# TCP or UDP server?
proto udp
# the firewall for the TUN/TAP interface.
dev tun
ca /etc/openvpn/easy-rsa/keys/ca.crt
cert /etc/openvpn/easy-rsa/keys/server.crt
key /etc/openvpn/easy-rsa/keys/server.key
# 2048 bit keys.
dh /etc/openvpn/easy-rsa/keys/dh1024.pem
server 10.8.0.0 255.255.255.0
# previously assigned.
ifconfig-pool-persist ipp.txt
# back to the OpenVPN server.
push "route 192.168.0.0 255.255.255.0"
client-to-client
keepalive 10 120
# enable it in the client config file.
comp-lzo
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
verb 3
client
dev tun
proto udp
resolv-retry infinite
nobind
persist-key
persist-tun
ca /etc/openvpn/easy-rsa/keys/ca.crt
cert /etc/openvpn/easy-rsa/keys/clientxxx.crt
key /etc/openvpn/easy-rsa/keys/clientxxx.key
comp-lzo
verb 3
pull
float
# /usr/local/sbin/openvpn --config /etc/openvpn/server.conf
Fri Nov 24 07:33:22 2006 OpenVPN 2.0.9 i686-pc-linux [SSL] [LZO] [EPOLL] built on Nov 20 2006
Fri Nov 24 07:33:22 2006 Diffie-Hellman initialized with xxxx bit key
Fri Nov 24 07:33:22 2006 TLS-Auth MTU parms
Fri Nov 24 07:33:22 2006 TUN/TAP device tun0 opened
Fri Nov 24 07:33:22 2006 /sbin/ifconfig tun0 xxx.xxx.xxx.xxx pointopoint xxx.xxx.xxx.xxx
Fri Nov 24 07:33:22 2006 /sbin/route add -net xxx.xxx.xxx.xxx netmask 255.255.255.0 gw xxx.xxx.xxx.xxx
Fri Nov 24 07:33:22 2006 Data Channel MTU parms
Fri Nov 24 07:33:22 2006 GID set to xxxxxx
Fri Nov 24 07:33:22 2006 UID set to xxxxxx
Fri Nov 24 07:33:22 2006 UDPv4 link local
Fri Nov 24 07:33:22 2006 UDPv4 link remote: [undef]
Fri Nov 24 07:33:22 2006 MULTI: multi_init called,
Fri Nov 24 07:33:22 2006 IFCONFIG POOL: base=xxx.xxx.xxx.xxx
Fri Nov 24 07:33:22 2006 IFCONFIG POOL LIST
Fri Nov 24 07:33:22 2006 client1,xxx.xxx.xxx.xxx
Fri Nov 24 07:33:22 2006 client2,xxx.xxx.xxx.xxx
Fri Nov 24 07:33:22 2006 client4,xxx.xxx.xxx.xxx
# openvpn /etc/openvpn/client.conf
Thu Nov 23 07:33:00 2006 OpenVPN 2.0.9 i686-pc-linux [SSL] [LZO] [EPOLL] built on Nov 20 2006
Thu Nov 23 07:33:00 2006 IMPORTANT: OpenVPN's default port number is now xxxxx, based on an official port number assignment by IANA. OpenVPN 2.0-beta16 and earlier used 5000 as the default port.
Enter Private Key Password:
Thu Nov 23 07:33:13 2006 LZO compression initialized
Thu Nov 23 07:33:13 2006 UDPv4 link local: [undef]
Thu Nov 23 07:33:14 2006 Initialization Sequence Completed
# ifconfig
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:xxx.xxx.xx.1 P-t-P:xxx.xxx.xx.2 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:60 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:2970 (2.9 Kb) TX bytes:0 (0.0 b)
tun1 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:xxx.xxx.xx.6 P-t-P:xxx.xxx.xx.5 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
OpenSSLによる認証 ▲ top
《 ■ 認証局証明書 ■ 》
# vi /etc/openvpn/easy-rsa/vars
export D=`pwd`
export KEY_CONFIG=$D/openssl.cnf
export KEY_DIR=$D/keys
# Issue rm -rf warning
echo NOTE: when you run ./clean-all, I will be doing a rm -rf on $KEY_DIR
export KEY_SIZE=1024
export KEY_COUNTRY=JP
export KEY_PROVINCE=Osaka
export KEY_CITY=Yao
export KEY_ORG="OpenVPN-test"
export KEY_EMAIL="tako@xxxx.ne.jp"
# cd /etc/openvpn/easy-rsa/
# . ./vars
NOTE: when you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
# ./clean-all
# ./build-ca
Generating a 1024 bit RSA private key
..........++++++
......++++++
writing new private key to 'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [JP]:
State or Province Name (full name) [Osaka]:
Locality Name (eg, city) [Yao]:
Organization Name (eg, company) [OpenVPN-test]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:OpenVPN-CA
Email Address [tako@xxxx.ne.jp]:
《 ■ サーバ証明書 ■ 》
# cd /etc/openvpn/easy-rsa/
# ./ build-key-server VPN_SERVER
《 ■ DH(Diffie Hellman)パラメータの作成 ■ 》
# ./build-dh
Generating DH parameters, 1024 bit long safe prime, generator 2
This is going to take a long time
...............................................+....
............................++*++*++*
《 ■ クライアント証明書 ■ 》
# # cd /etc/openvpn/easy-rsa/
# ./build-key-pass clienta
Generating a 1024 bit RSA private key
.........................++++++
...........++++++
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
Common Name (eg, your name or your server's hostname) []:client1
# cd /etc/openvpn/easy-rsa/
# ./build-key-pass clientd
you must define KEY_DIR
# cd /etc/openvpn/easy-rsa/
# . ./vars
NOTE: when you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
# ./build-key-pass client4
ルータの設定 ▲ top
# iptables -A INPUT -i tun+ -j ACCEPT
# iptables -A INPUT -p udp --dport 5000 -j ACCEPT
# iptables -A OUTPUT -p udp --dport 5000 -j ACCEPT
# iptables -A FORWARD -i 外部-INTERFACE -d サーバIP -p udp --dport 5000 -m state --state NEW,ESTABLISHED,RELATED -j ACCEPT
# iptables -A FORWARD -o 外部-INTERFACE -s サーバIP -p udp --dport 5000 -m state --state ESTABLISHED,RELATED -j ACCEPT
Windowsへのインストール ▲ top
http://openvpn.se/files/install_packages/openvpn-2.0.9-gui-1.0.3-install.exe
ca.crt (認証局証明書) clientA.crt (クライアント公開鍵) clientA.key (クライアント秘密鍵)
client
proto udp
dev tun
remote 61.xxx.xxx.123 5000
ca ca.crt
cert clientxxx.crt
key clientxxx.key
resolv-retry infinite
nobind
comp-lzo
persist-key
persist-tun
verb 3
pull
float
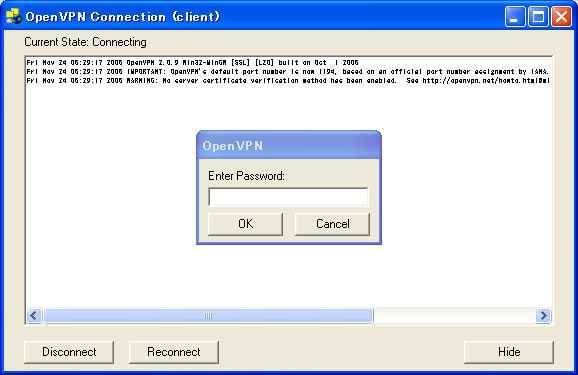
Macへのインストール ▲ top
Tips ▲ top
補記
| 《 ■ 参照URL ※サイト内参照ページ 引用、参照書籍 ■ 》 |
| OpenVPN |
| OpenVPNで構築するリモートアクセス環境 |
| OpenVPN 2.0 HOWTO 日本語訳 |
| ※ OpenSSL |
| ※TCP/IP(Transmission Control Protocol/Internet Protocol) |
| 『VPN構築術』 著/一条博 2004年7月発行 刊/工学社 |
| 『超簡単VPN入門』 著/ケインズプロダクション 2006年9月発行 刊/タトルズ |
![]()
![]()
![]() ▲ top
home:top
server library:top
PHP PostgreSQL MySQL サンプルスクリプト
SiteMap
Open SiteMap
▲ top
home:top
server library:top
PHP PostgreSQL MySQL サンプルスクリプト
SiteMap
Open SiteMap